Don’t take the bait: how to resist phishing tactics
One of the most common forms of online fraud is phishing. Its aim is to obtain confidential data or login details from users. It can appear in your email inbox, on social media or come in the form of a text message. On International Computer Day, Brno University of Technology is urging students and staff to be vigilant and offers guidance on how to respond to phishing (not only) at BUT.

What is phishing
Phishing (a variation of the word fishing) is a technique used by scammers to obtain confidential data from users. It consists of sending emails, private messages on social networks or text messages masked as good deals, threats or notifications from familiar organisations.
Like all of IT, phishing and other forms of online scams are constantly evolving and becoming more sophisticated – phishing is now much more commonly encountered in a targeted form, where the message contains graphic elements of the attacked organisation. The pages to which the scam links are directed are often a faithful copy of an organisation's website.
The attackers' goal is to:
- Access our data
- Obtain the data of the organisation whose services we use (e.g. BUT)
- Deploy malware (a malicious application or code that damages a device) on a user's device
The obtained data often ends up in databases on the so-called dark web, where it is sold by scammers. This is also why it is important not to share passwords between multiple services.
Both desktop and laptop users are vulnerable, as well as users of mobile devices such as smartphones and tablets, where identifying phishing is a little more difficult.
How to spot phishing
Whenever you receive an unexpected message, whether by email, text message or in private messages on social media, look at it carefully.
The most common signs of phishing include:
- Generic form of address (e.g. “dear friend”)
- Poor grammar, stylistics or foreign language
- Urgent tone or threatening language
- The presence of links that usually lead to a page requesting login details
The message may also contain strange looking attachments (often in a ZIP file) with unintelligible or generic names. These may harbour computer viruses.
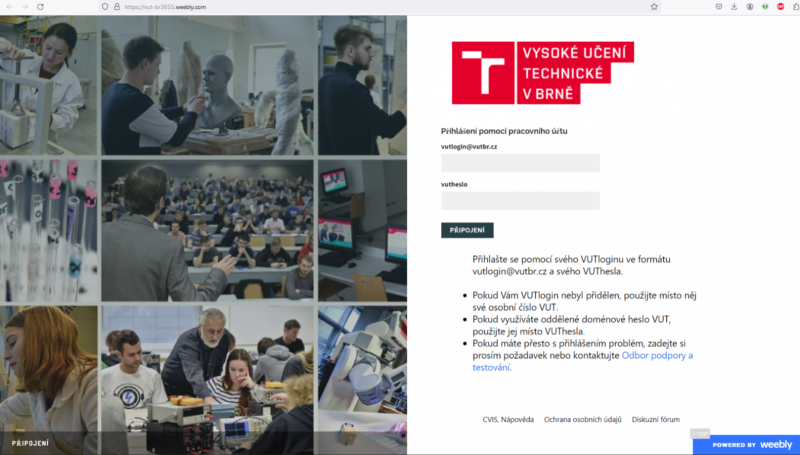
How to respond to phishing
- Always double-check the sender
- Do not automatically download attachments
- don't click hastily on links – in the case of web applications, always check that the address (URL) contains https:// at the beginning and that the address itself contains the domain vut.cz, vutbr.cz or google.com if logging in via Google or microsoft.com if logging into Microsoft services before the first single slash
- If you do click through, look at the page carefully and do not enter any data! Inaction is always safer in this case
- As a precaution, it is important to update your antivirus software regularly
Did you take the bait? Don't be indifferent and take action!
Even with thorough prevention, it can happen that a user gets caught. Attacks are often very sophisticated. That is why it is good to know what to do in such a situation:
- If you can, change your password immediately and report the incident to the BUT Centre of Information Services (CIS BUT) as soon as possible using the request system (area "CIS Services, General Requests, Cybersecurity").
- If this does not work, it is possible that our account has been compromised and blocked. We can find out the procedure if we cannot log in on the CIS BUT website. Most likely, we will need to visit the local administrator at the faculty or unit, see the CIS website, or the student services department. Bring your ISIC or staff card
- Report the email or message in the email interface as phishing or spam
Useful information about phishing and how to defend yourself against it in English is available for example at the European Union Agency for Cybersecurity website.
Source: vut.cz/en
| Responsible person | Ing. et Ing. arch. Jana Němcová |
|---|---|
| Date of publication |

